Troubleshooting
This topic provides some insights into various error scenarios that you might encounter.
Also see OAuth2 error responses
Diagnostics
Unit4 Identity Services (U4IDS) uses Serilog for application-wide logging. This is configured in the web.config file. Learning how to investigate the log is a great way to diagnose issues encountered.
Invalid scope
Possible causes
- Scope is not registered in the scope repository (check discovery endpoint for available scopes)
- It is not a valid scope for the client
- Requests for id_token response type only must not include resource scopes
For more details on the difference between ID scope and resource scope, see Scope.
Invalid response type
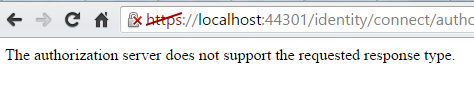
Possible causes
- Missing response_type in the request
- Response type not supported. The supported response types are:
- code
- token
- id_token
- token id_token
- code id_token
- code token
- code id_token token
- Invalid response_mode for flow (form_post, fragment, query). See Flows supported response types for the different types of flows.
- Unsupported response_mode
If the response type is not valid the request will not reach the authentication middleware, therefore this will not produce any logging information. Check the listed parameters and see which one is wrong.
Invalid token
This typical happens if you only copy a part of your access token or reference token or if you by an accident has a typo. If you have an jwt token you can use jwt.io to check if your token is valid.
Possible causes
- Invalid reference token
- Invalid access token
Invalid request
This often happens when you are missing a required parameter in the request. Note: Different required parameters for different authentication flow see flows
Possible causes
- Missing parameters in the request:
- Verify that you have the tenant information in the acr_values parameter. E.g. "&acr_values=tenant%3aInnovation corp".
- Verify you have the
openidscope - Verify the redirect_uri matches the redirect_uri registered on the client
Invalid client
You will get error message invalid_client from the token endpoint (not authorize endpoint) or revocation endpoint if you request clientId or secret property is invalid.
Possible causes
- Wrong credentials:
- Invalid client secret (Your client secret is wrong)
- Invalid client id (Requested ClientId not found)
The client application is not known or is not authorized
You will get an unauthorized client when the client configuration does not match the authorize request.
Possible causes
- Client is not enabled (check enables property on your registered client)
- Redirect uri is Invalid
- Requested scope is not allowed (check AllowedScopes property on the registered client)
Please contact your system administrator
You should open the log on your U4IDS to see more information.
Possible causes
- Certificate issue
- Verify that signing certificate thumbprint is configured
- Verify that the certificate exists in the specified certificate store
- No signin id
- Invalid request parameters:
- acr_values does not contain tenant or tenant is not registered
- Invalid redirect uri
- ClientId is not registered (does not exist)
- Response type does not match the clients registered flow (for example
code tokenis not a valid option for implicit flow)
- No identifier claim from external identity provider
- Case inconsistency in cookie path value
Case inconsistency in cookie path value
The requests base path will be used as cookie path value. The cookie path value is treated as case sensitive by the browser. If the request to U4IDS is different from the redirect url to the Identity Provider this will cause that the cookies are not transferred back to U4IDS.
*Make sure U4IDS base path from the request matches the case on the U4IDS server. *
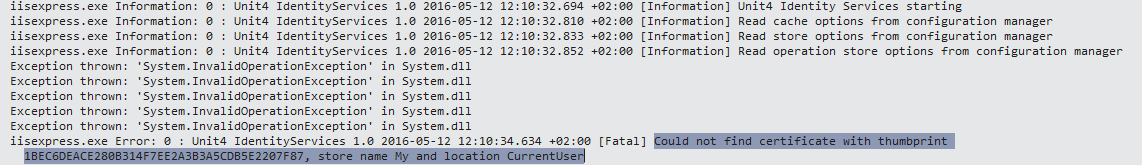
Certificate issue
The certificate must be uploaded to Azure for Azure deployment.
Could not find certificate with thumbprint XXX, store name XXX and location XXX
Causes
- Certificate must be uploaded to Azure Web Site
- The Identity server does not have access to the store location, make sure WEBSITE_LOAD_CERTIFICATE app setting is set.
Logging
Note
The certificate thumbprint copied from MMC snapin has an invisible extra space at the beginning of the string. It must be removed. See this article for details.
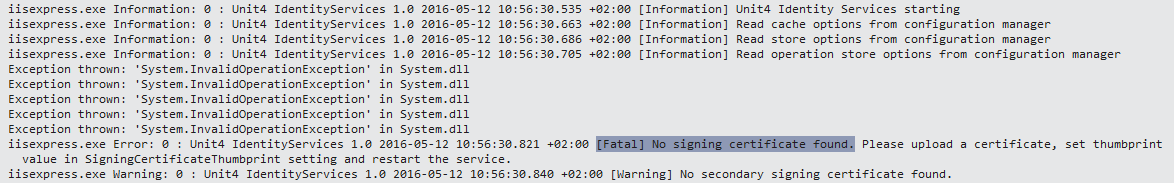
No signing certificate configured
Causes
Requires a certificate to be installed on the server certificate store.
Logging
No signin id
Possible causes
- Missing parameters in callback
- If you went directly to the login page without going first going thru the authorization endpoint
- Your tenant authority property is invalid
- Case inconsistency in Cookie path value (see topic above)
Missing parameters in callback
After a sucessful login, the IdP should call the U4IDS callback endpoint. The user is able to login but the callback to IDS is showing Please contact your system administrator.
Verify that your callback has a SigninMessage cookie and a state in the form post.
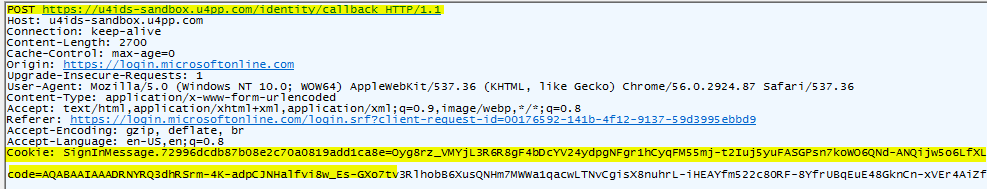
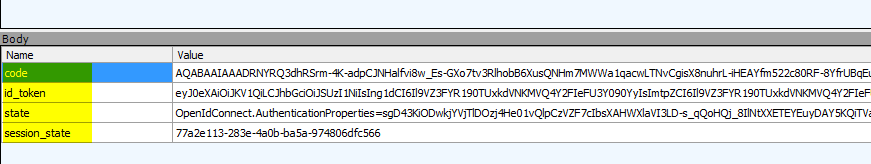
- Missing state in callback: The state is not sent back to the U4IDS callbak endpoint after a sucessful login.
- SigninMessage cookie is missing: SigninMessage is removed from the IDS callback request
- Configuration changes: The user has logged in before you do a configuration change (for example changes in client). The user should logout and login again.
- Previous request/response happened in https while this request in http: IDS for some reason is not configured with HTTPS or there is a mixed requests between http and https.
From IDS log
[Information] Callback invoked from external identity provider
[Information] No signin id passed
ADFS Deep-Dive: Comparing WS-Fed, SAML, and OAuth
WS-federation: wctx parameter missing
No identifier claim from external identity provider
After authenticating the external identity provider calls the U4IDS callback with the authentication token. The token needs to contain identifier claims. There are two claim types:
- sub
- http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier
From IDS log
[Error] no subject or unique identifier claims from external identity provider. Claims provided:
