OKTA authentication configuration Openid
This how-to guide describes how to configure Unit4 Identity Services with OKTA Openid Connect.
Prerequisites
- Administrative access to OKTA
- Knowledge of OKTA and how to create an OKTA application
- U4IDS authority address (in the rest of this topic we use
https://<address of U4IDS installation>/identityas the address of the U4IDS installation's identity endpoint with sample valuehttps://u4ids-sandbox2.azurewebsites.net) - Access to U4IDS in order to create tenant
The list of official IDS environments can be found here
Steps
Setup trust between U4IDS and your OKTA as follows:
- Register U4IDS as an application in OKTA
- Create a new OKTA application
- Set the redirect URIs
- Get Client id and secret
- Get the authority
- Register the OKTA application as a tenant in U4IDS
- Select a unit4IdClaimType
- Set the idpRegId and idpSecret
Register U4IDS as an application in OKTAa
Follow these steps:
Create a new OKTA Application
Create a new Application on your OKTA account by clicking Create Application button in the Applications section.
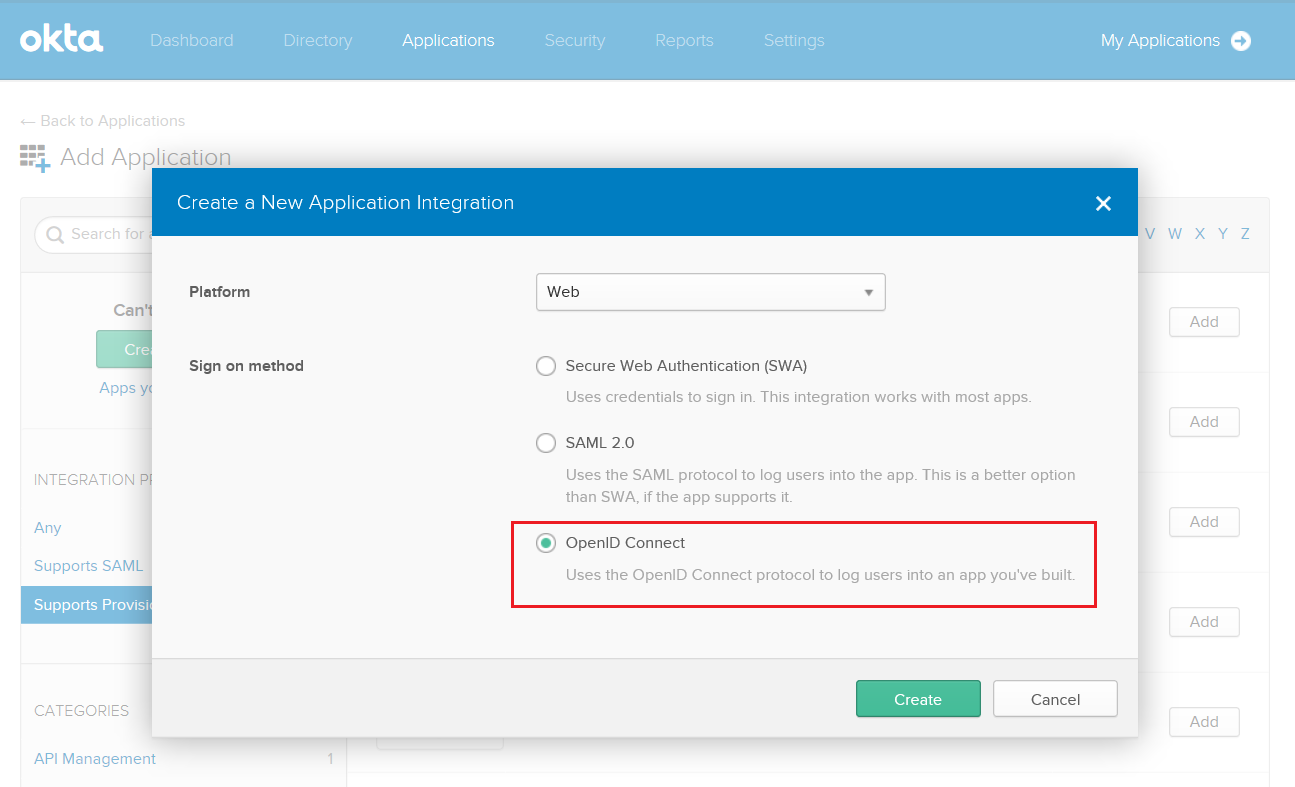
Select Open ID Connect as the authentication method.
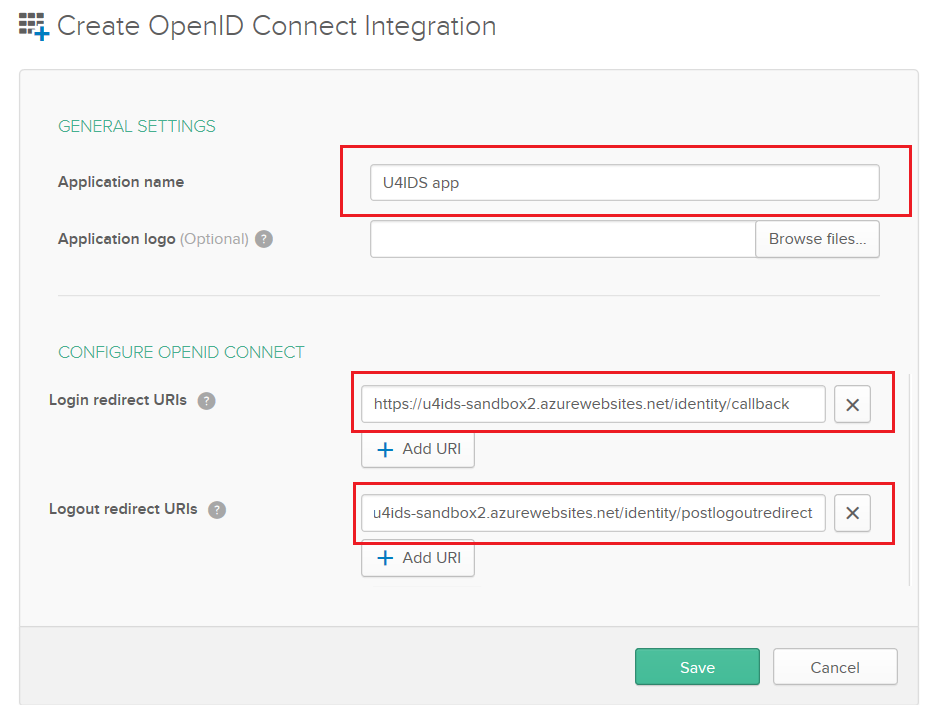
Give the application a name indicating that it is used for U4IDS authentication.
Set the redirect URIs
Enter the U4IDS callback URL in Login Redirect URIs field following the pattern https://<address of U4IDS installation>/identity/callback where on the image the address of U4IDS installation is https://u4ids-sandbox2.azurewebsites.net.
Enter the U4IDS logout URL in Logout Redirect URIs field following the pattern https://<address of U4IDS installation>/identity/postlogoutcallback
Save the changes and Edit the data again to correct the Initiate login URI value by trimming the trailing /callback text.
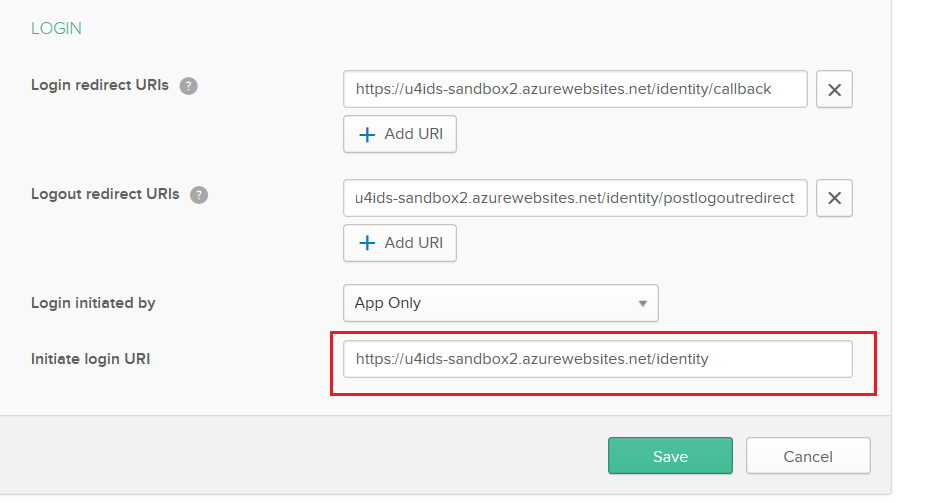
Also change the Allowed grant types by adding there Implicit flow with allowing ID Token with implicit grant type.
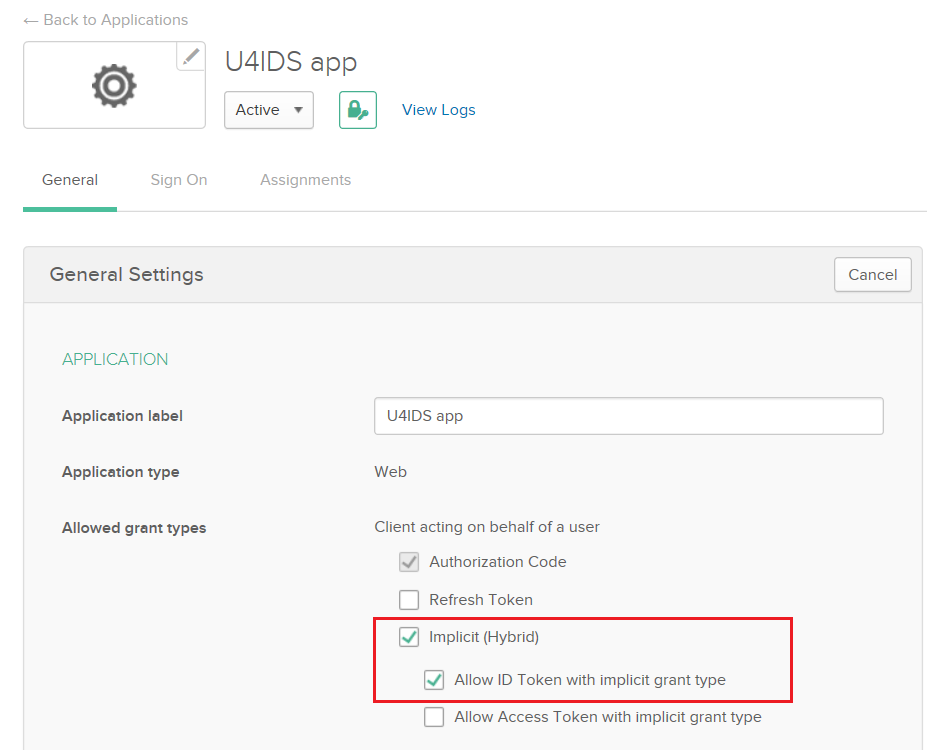
Get Client id and secret
In the section Client Credentials there are two fields of which data are needed to configure a Tenant in U4IDS.
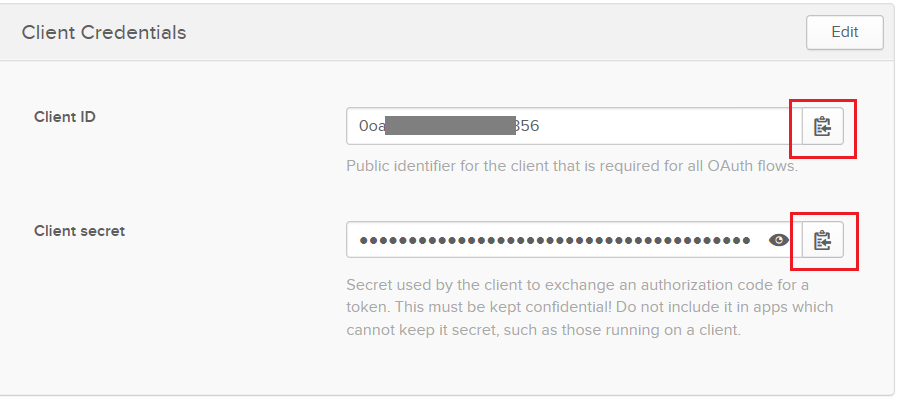
Copy over the Cilent ID and Client secret data to use in the Tenant setup in U4IDS. If needed you could regenerate the client secret, mind that for a configuration that is already setup between U4IDS and OKTA, this would result in breaking the connection. The new Client secret data would need to be updated in U4IDS to repair the connection.
Get the authority
To locate the OKTA directory authority value (we need to configure Tenant in U4IDS) go to application's Sign on tab. In the Open ID Connect ID Token section you will see the Issuer value to be copied: