Architecture overview
The Unit4 Identity Services (U4IDS) is an OpenId Connect provider built on top of Thinktecture IdentityServer. U4IDS acts as a gateway between the client application and the registered company's (tenants) Identity Provider (IdP).
U4IDS components
An overview of the components in U4IDS is shown below.
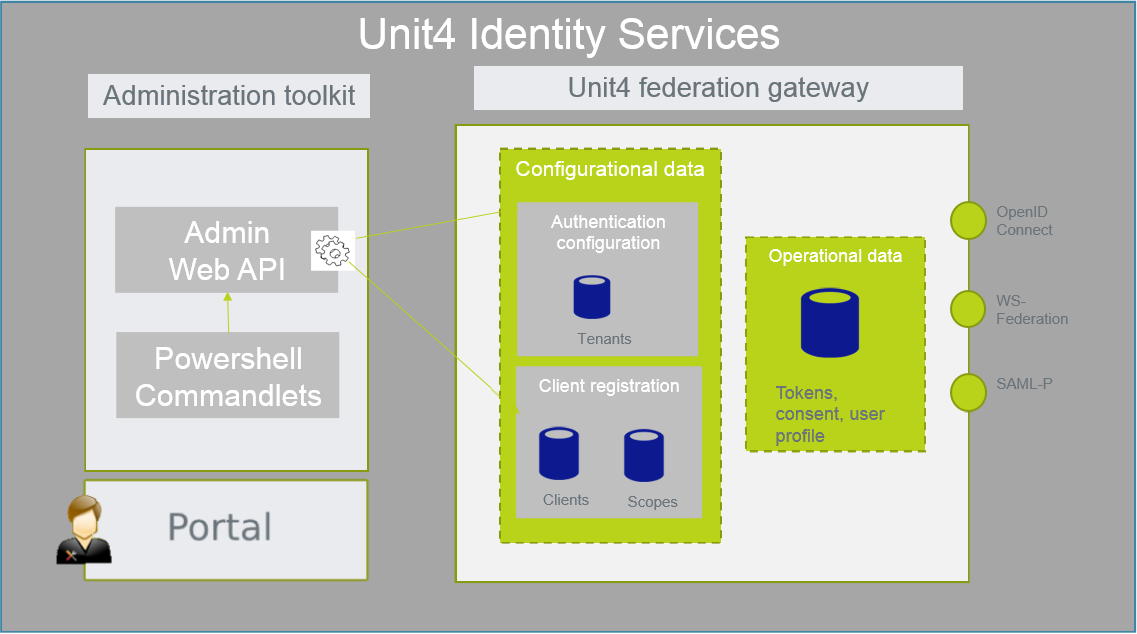
- Unit4 Federation gateway - U4IDS does not authenticate the client, but relies on the tenant's external IdP, a federation gateway between the client and customers identity provider.
- Configurational data
- Client registration - A trust relationship is required between the client and the Identity Server. To setup trust the Unit4 product (client) must be registered in the client store.
- Tenant registration - Here the customer configures which Identity Provider they want to use to authenticate users.
- Operational data - Store for operational data. This includes authorization codes, refresh tokens, reference tokens and external refresh tokens.
- Configurational data
- Administrator toolkit - The administrator toolkit contains tools for an administrator to register tenants and clients
- Admin API - Web APIs to register client, tenants and scopes.
- Powershell commandlets - Commandlets that help administrators automate the registration of clients and tenants.
Portal
The Identity Services Portal is a website that supports and simplifies the configuration and maintenance of the Identity Services, as well as the creation and operation of clients, the tenant and users, granting or denying access.
Users included in Azure Active Directory, authenticate in U4IDS Portal using their user credentials, and are authorized using the information configured in Unit4 Access Management System. This information includes a role per user, different from the one configured in U4IDS Access Management System, that determines what operations they are allowed to perform. These roles are:
| Role | Permissions |
|---|---|
| None | User cannot access U4IDS Portal. |
| Reader | User can perform read operations on U4IDS resources, but cannot modify anything. |
| Contributor | User can manage U4IDS resources but cannot manage users nor modify settings. |
| Owner | Full access to all operations. |
Users without access to U4IDS Portal can request it when logging in.
Authentication flow
The sequence diagram below illustrates one of the authentication flows where the client application authenticates against the tenants identity provider using U4IDS.
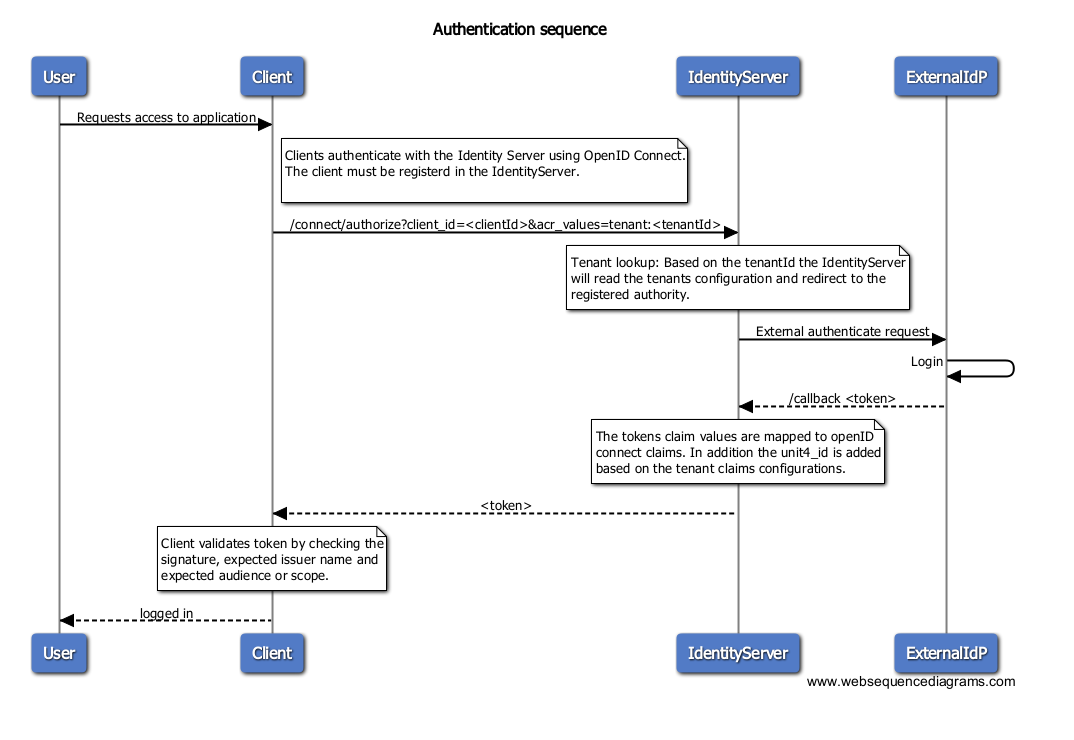
- Request access to the application - The user is not authenticated and requests access to the client application.
- Client request authentication - The client calls the Identity Services to authenticate the user. The client sends the clientId and tenantID.
- Client validation - The Identity Services validates the client based on the sent clientId.
- Tenant lookup - The Identity Services finds the tenant configurations based on the tenantId sent by the client.
- External authentication request - The Identity Services redirect to the external Identity Provider. Based on the requested tenants configuration the Identity Services finds the external IdP, authority, and redirects.
- User login - The user is provided with the external IdPs login screen.
- Callback - When the user is successfully logged in it returns back to the Identity Services with a token (can be access token and id token, depending on the flow).
- Claims mapping - Maps incoming claims to OpenID Connect claims and in addition a unit4_id claim.
- Redirect to client - U4IDS redirects back to the client.
