Google configuration
This how-to guide describes how to configure Unit4 Identity Services with Google.
Prerequisites
- A Google account
- Knowledge of Google and how to create a Google application
- U4IDS authority address (in the rest of this topic we use the value of
https://<u4ids basepath>/identityas the address of the U4IDS installation's identity endpoint) - Access to U4IDS in order to create tenant (Portal or Powershell)
The list of official IDS environments can be found here
Steps
Setup trust between U4IDS and Google as follows:
- Register U4IDS as an application in Google
- Create a new Google client
- Get client id and secret
- Register the Google application as a tenant in U4IDS
- Select a unit4IdClaimType
- Get the authority
- Get the idpRegId
- Get the idpSecret
Register U4IDS as an application in Google
Follow these steps:
Create a new Google client
You need to have a google account to login. Create one if you need to:
Log in to Google: and choose select a project and click "Add project":
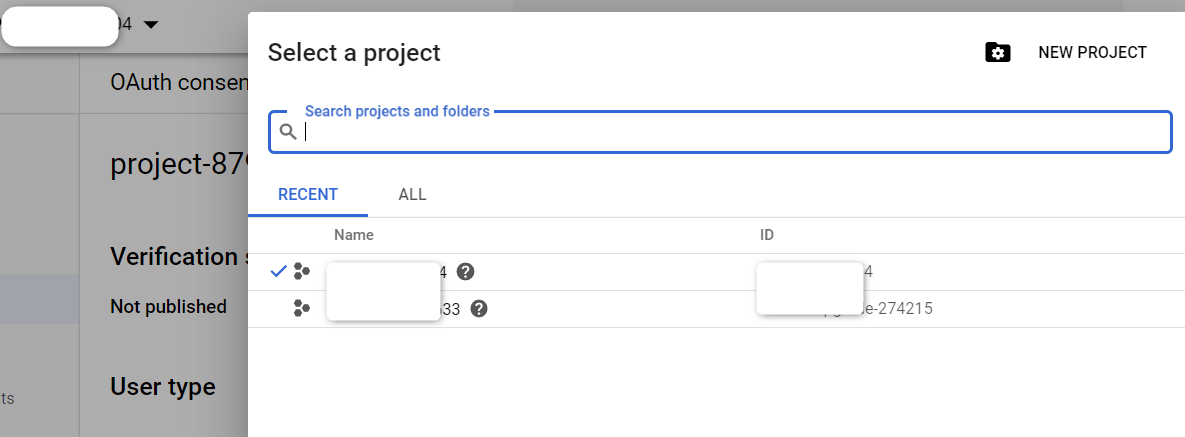
Give the project a descriptive name and click the CREATE button.
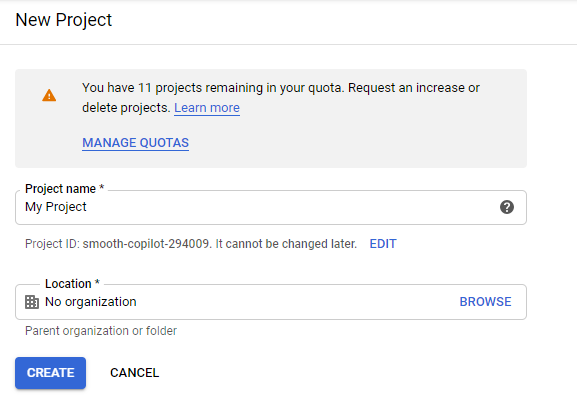
If the APIs & services page isn't already open, open the console left side menu and select APIs & services. Then click Credentials on the left side:
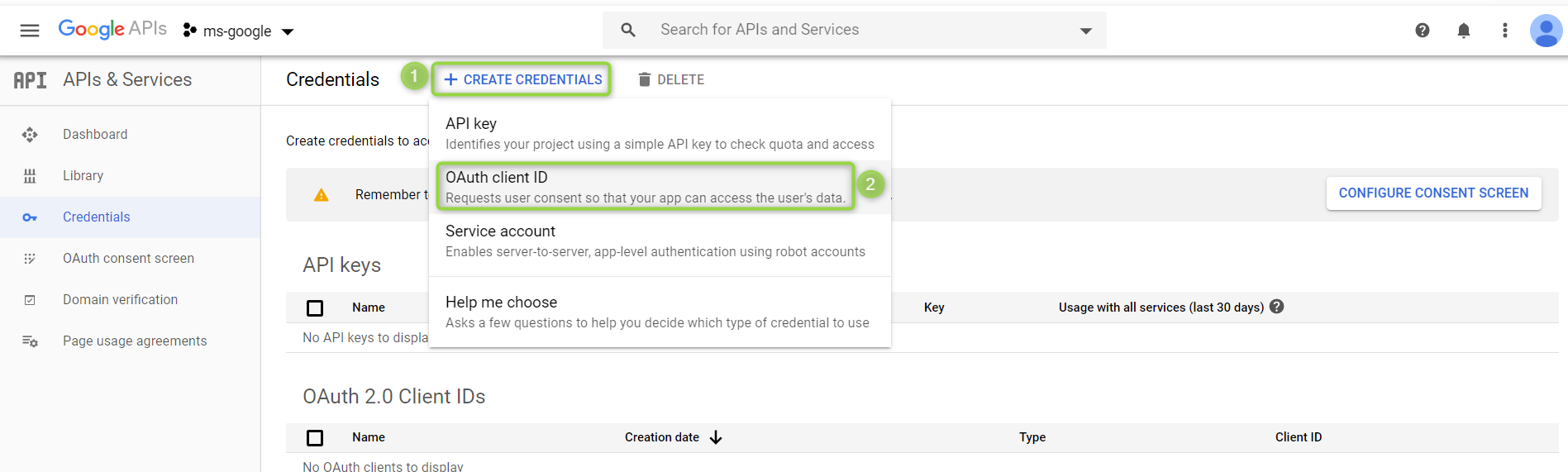
Click "Create credentials" and from the drop-down list choose "OAuth client ID".
If you havent configured consent previously you need to click "Configure consent screen" to provide the information displayed to users whenever they try to log in to IDS through Google.
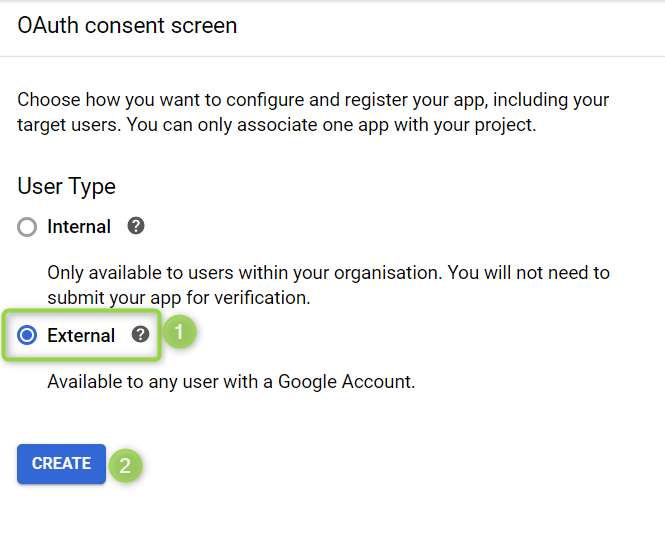
In the respective fields, type your Email address and Product name. Optionally, you can provide your Homepage URL, Product logo URL, Privacy policy URL, and Terms of service URL. Scopes are identifiers for users or resources that a client wants to access. This identifier is sent to Unit4 Identity Services (U4IDS) during an authentication or token request. U4IDS supports two types of scopes:
- Identity scopes
- Resource scopes
Requesting identity information (claims) about a user, for example name or email address is modelled as a scope in OpenID Connect. There is, for example, a scope called profile that includes first name, last name, preferred username, gender, profile picture and more
Click Save to proceed.
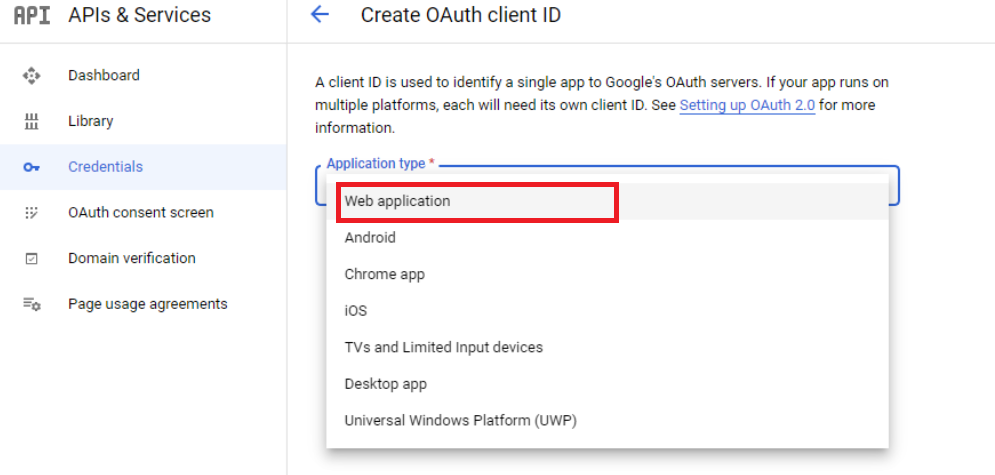
Go back to the Credentials screen and click create credentials "OAuth client ID" again. Select "web application" in the dropdown list.
Add a name and the allowed redirects to IDS.
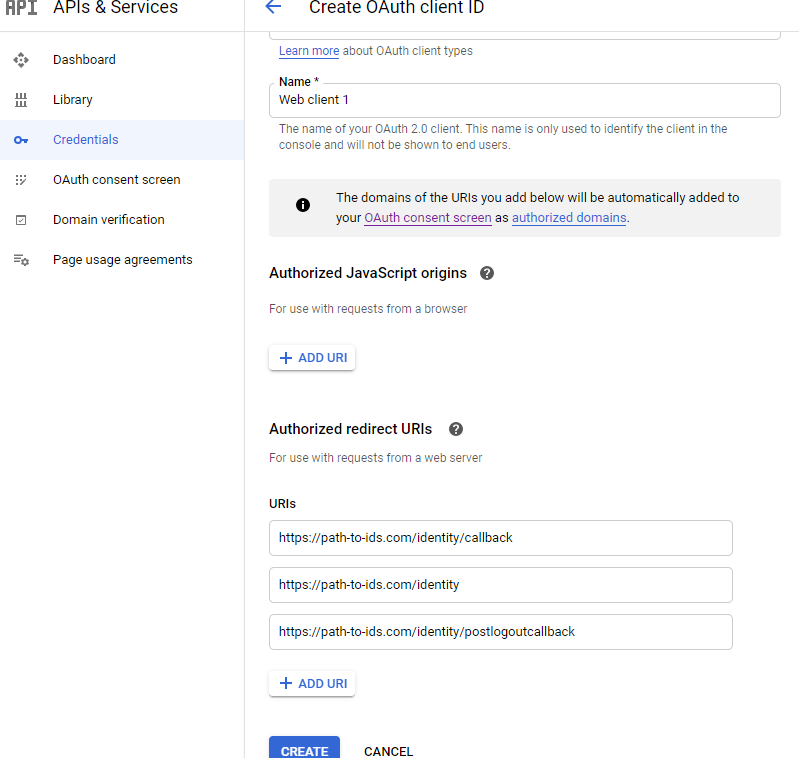
Click "create"!
Get client id and secret
Get client id and secret from creating the web application
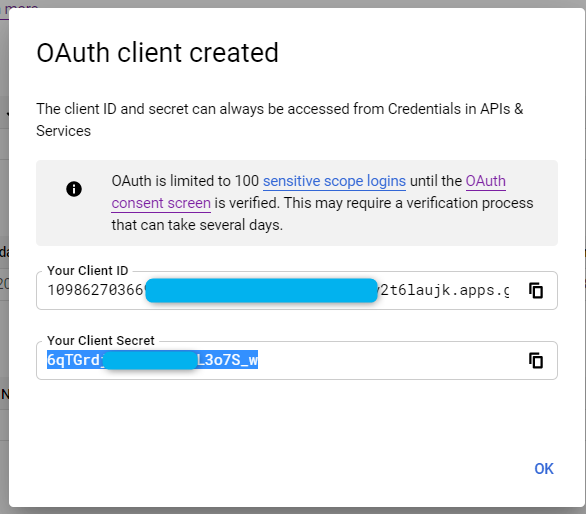
Save them away for registering the IDS Tenant.
Register the Google application as a tenant in U4IDS
After the above steps are done, the collected information may be inserted into the Tenant resource in U4IDS:
See Identity providers in tenants for more information.
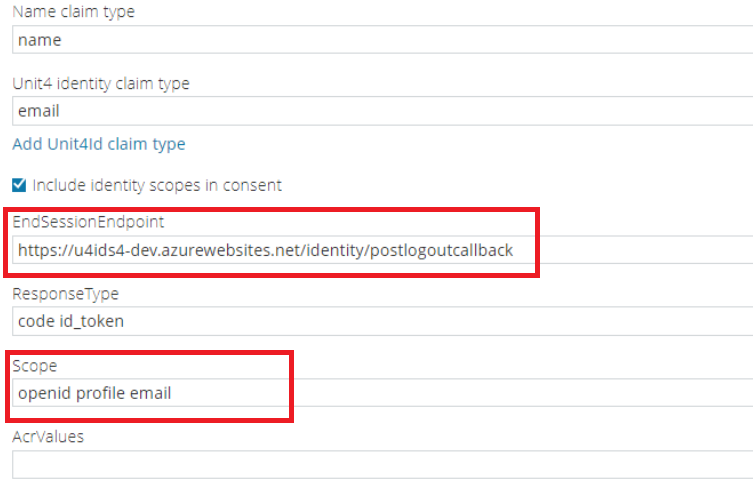
Select a unit4IdClaimType
For the unit4IdClaimType choose a unique claim that is available and preferably human readable. You can choose multiple claims. Then the first available claim in the order they are specified will be used.
Get the authority
Authority is "https://accounts.google.com/.well-known/openid-configuration"
Get the idpRegId
The idpRegId is the Google client id.
Get the idpSecret
The idpSecret is the Google client secret.
Note: Google dont support the offline_access scope or an end session endpoint. So it might be a good idea to use the openid override parameters to override these values: