Azure Active Directory SAML configuration
This how-to guide describes how to configure Unit4 Identity Services with Azure Active Directory (AAD) with SAML.
Prerequisites
- Administrative access to Azure Active Directory (AAD)
- Knowledge of AAD and how to create an AAD application
- U4IDS authority address (in the rest of this topic we use the value of
https://<u4ids basepath>/identityas the address of the U4IDS installation's identity endpoint) - Access to U4IDS in order to create tenant
The list of official IDS environments can be found here
Steps
Setup trust between U4IDS and your AAD as follows:
- Register U4IDS as an application in AAD
- Create an Enterprise application
- Configure application
- Find unit4 Tenant values
- Register the AAD application as a tenant in U4IDS
- Select a unit4IdClaimType
- Get the authority
- Get the idpRegId
Register U4IDS as an application in AAD
Follow these steps:
Create an Enterprise application
Choose the correct AAD if you have access to multiple AADs
Log in to Azure portal: https://portal.azure.com/ and go to Azure Active Directory:
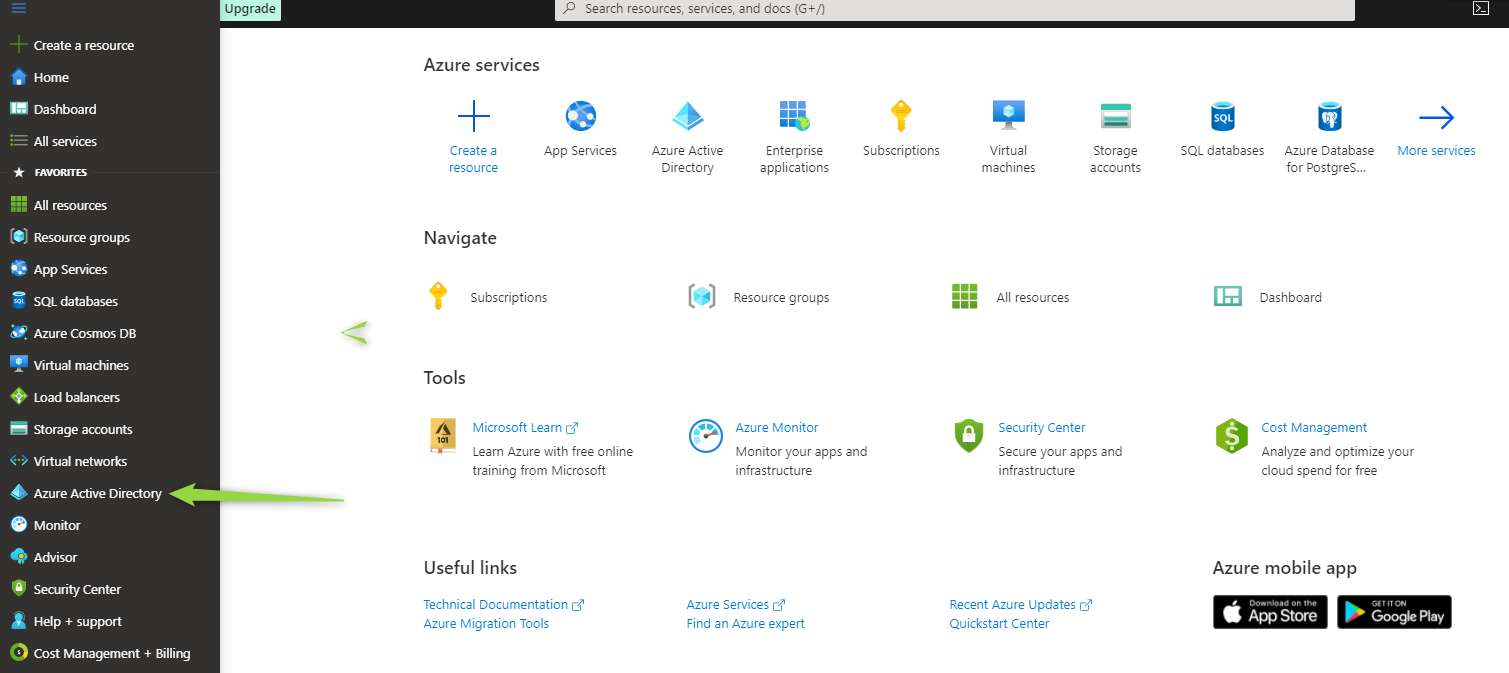
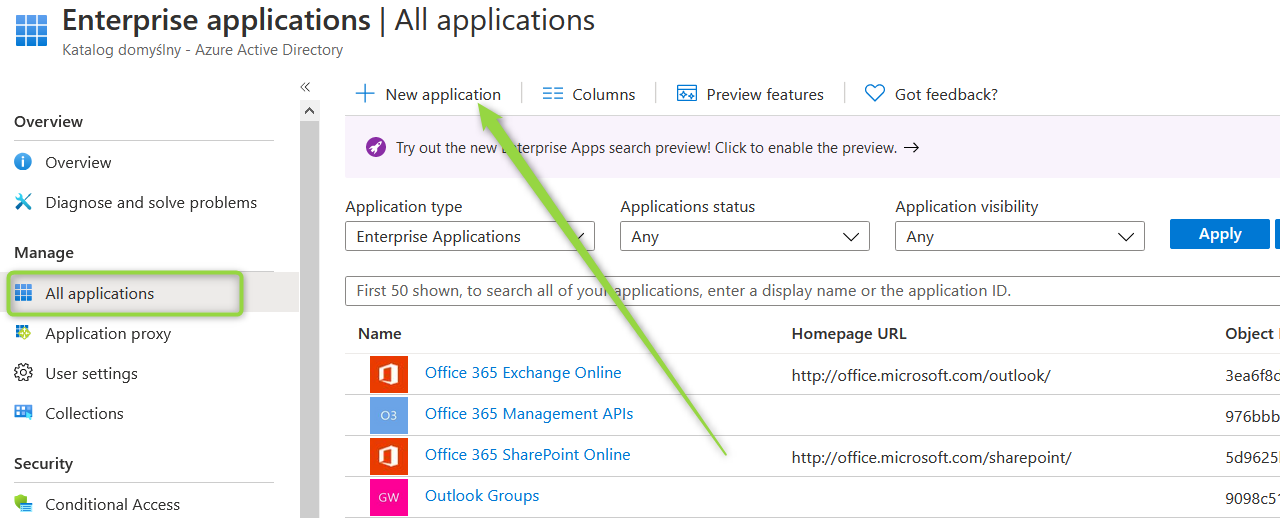
Go to "Enterprise applications", click "All applications" and create "New application"
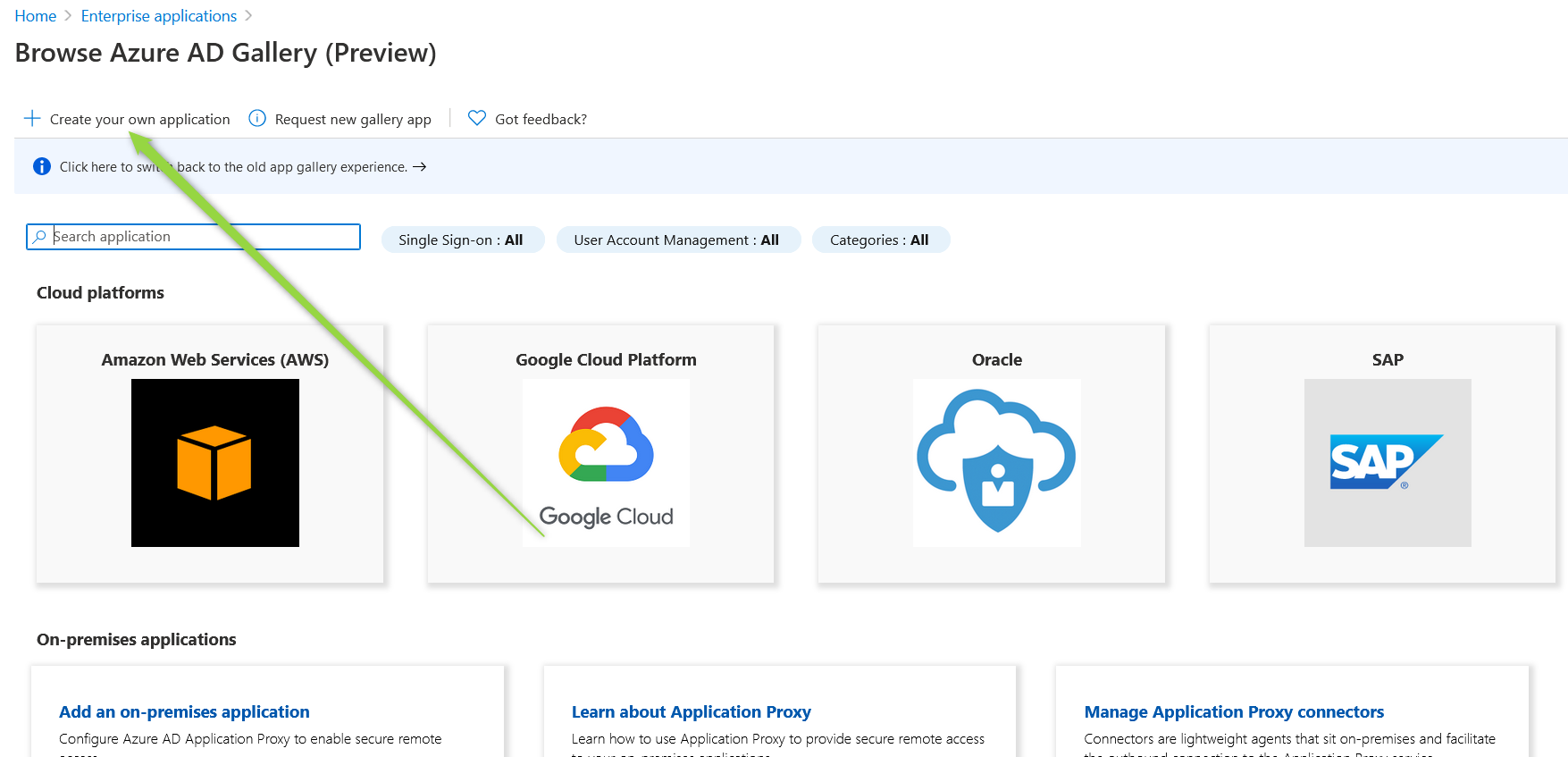
Click "Create your own application"
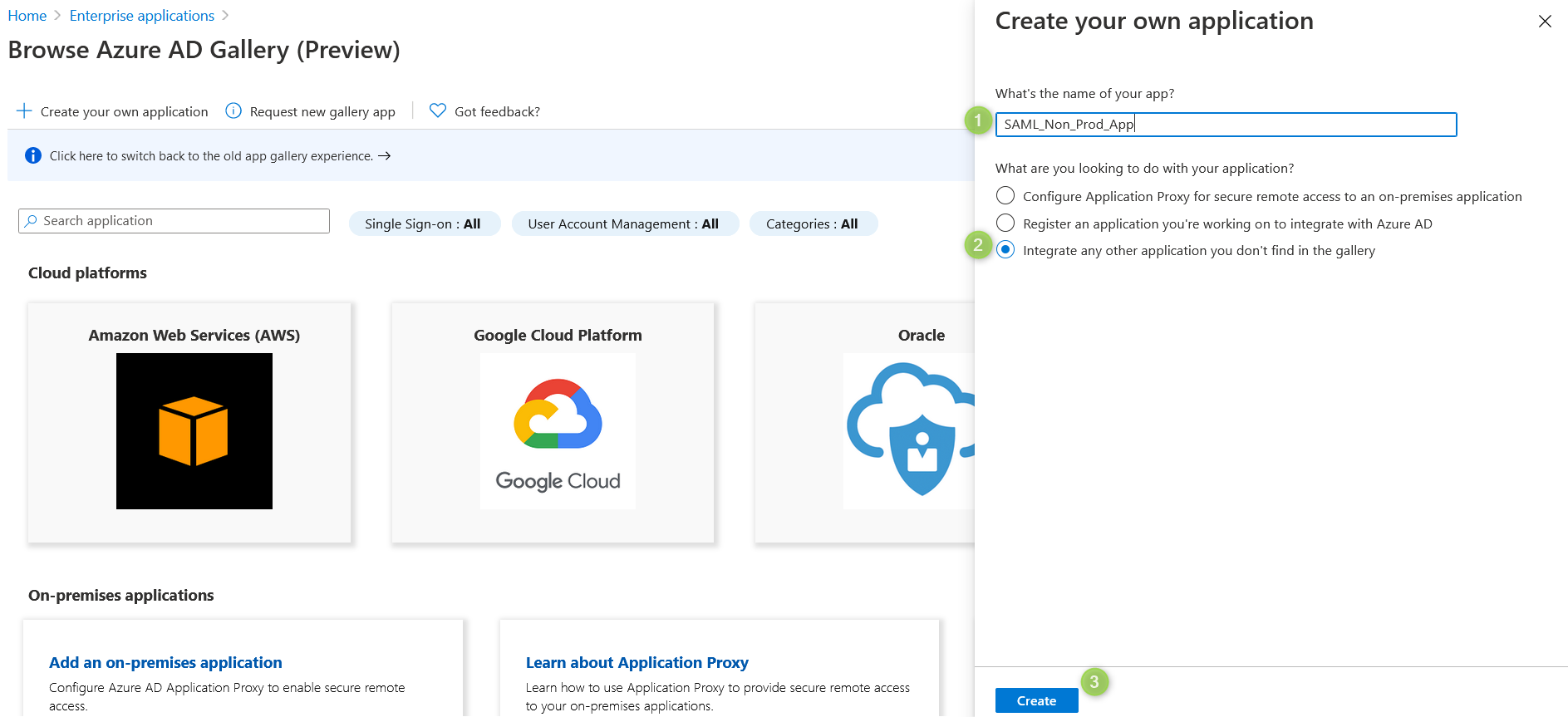
Enter your application name. Make sure "Integrate any other application you don't find in the gallery" is selected and click "Create".
Configure application
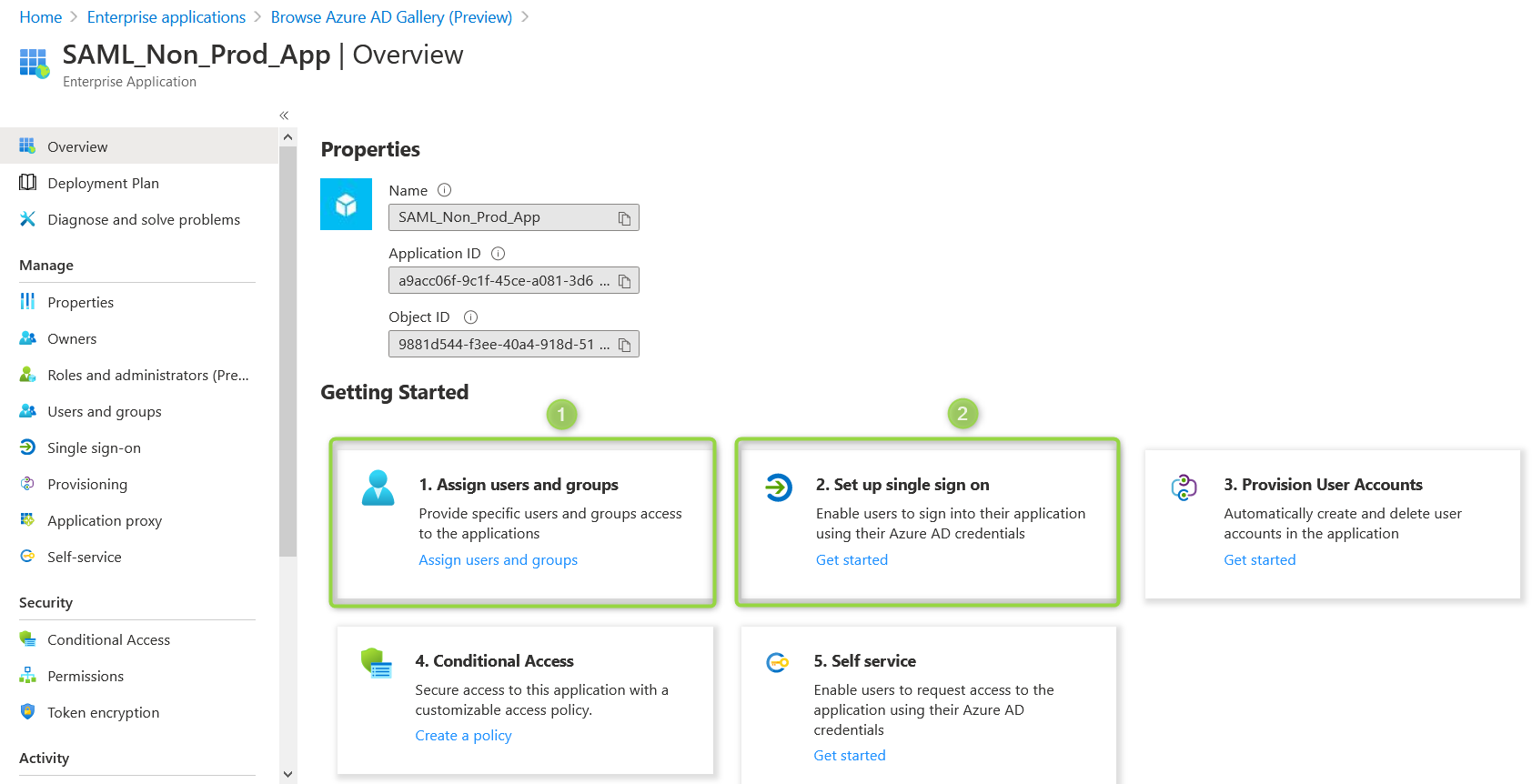
- First assign the users and groups you want to grant access to.
- Then choose to set up SSO parameters.
From the single sign-on menu choose SAML
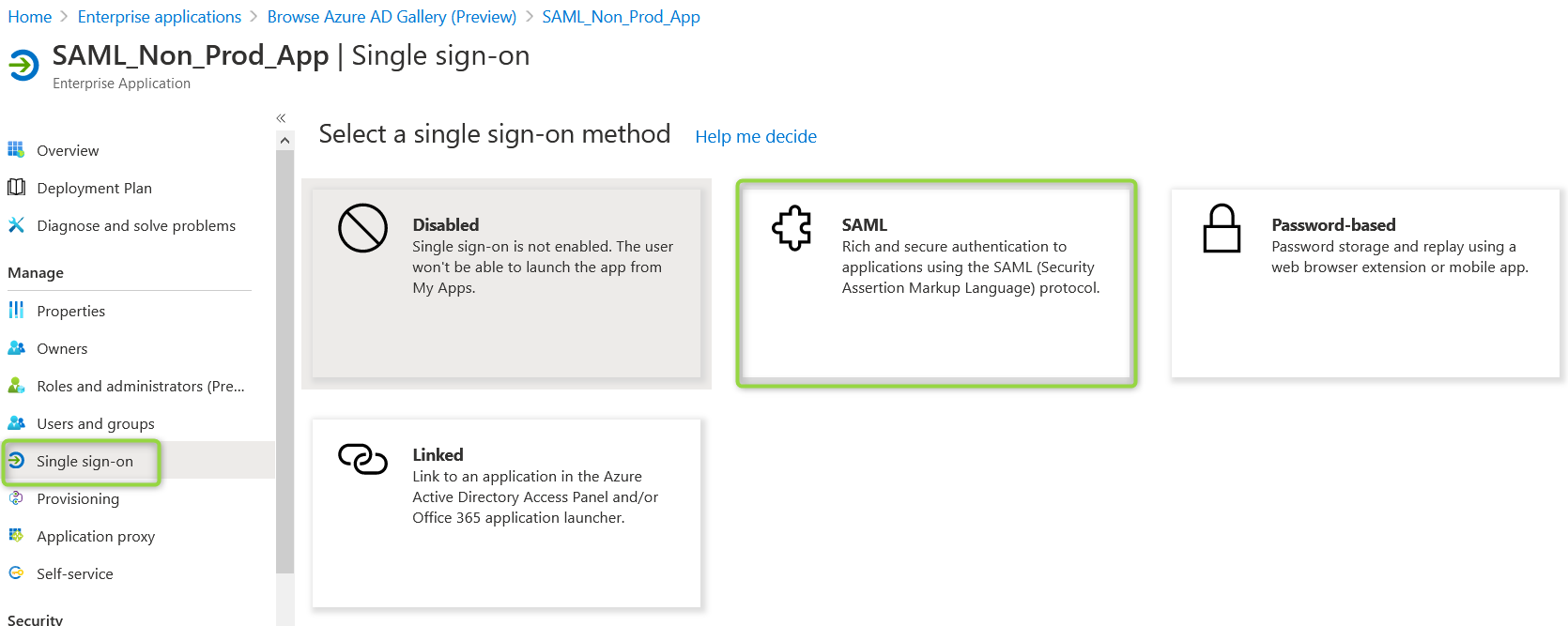
In the SAML-based Sign-on screen you can chose to: (1) Upload a metadata file (Links for proper region and instance type are located in "SAML redirect urls per region") or (2) Enter links manually
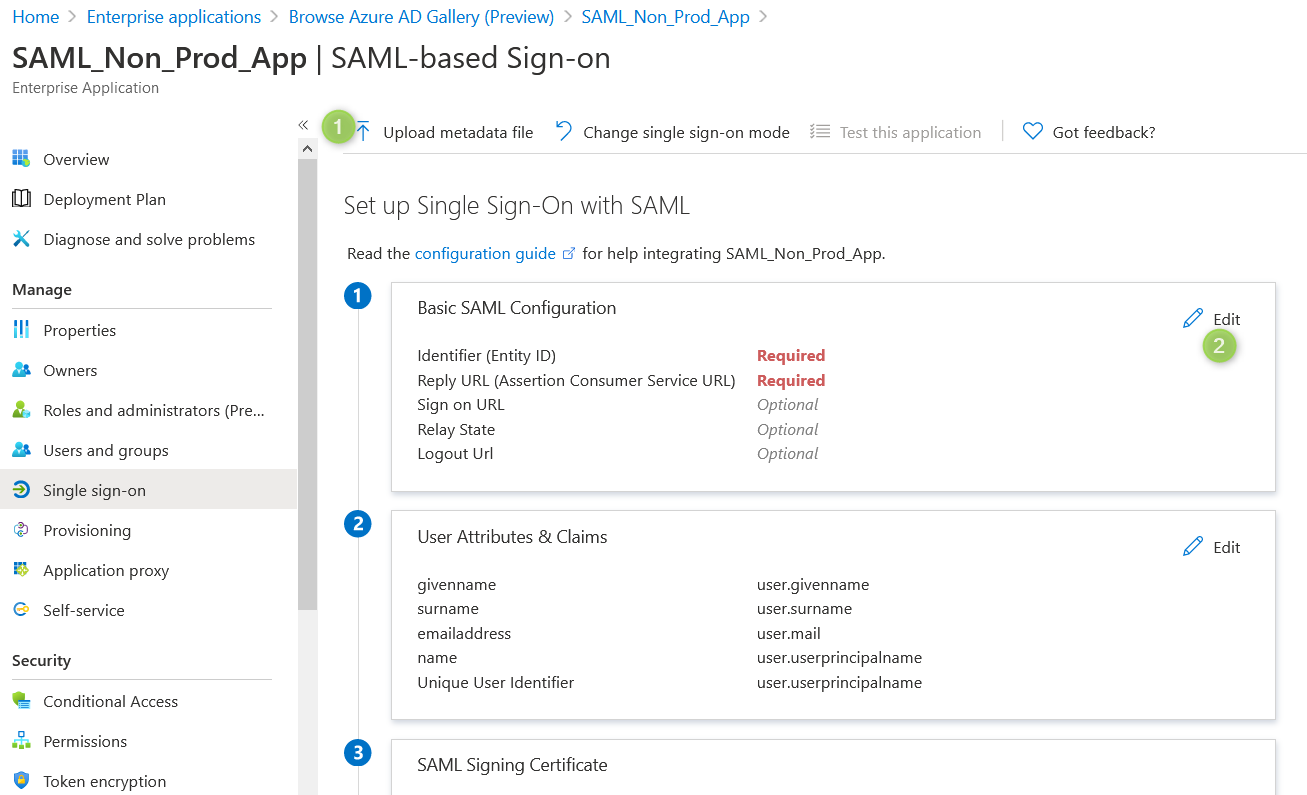
In Basic SAML configuration. Make sure that "Relay state" has the same value as "Entity ID".
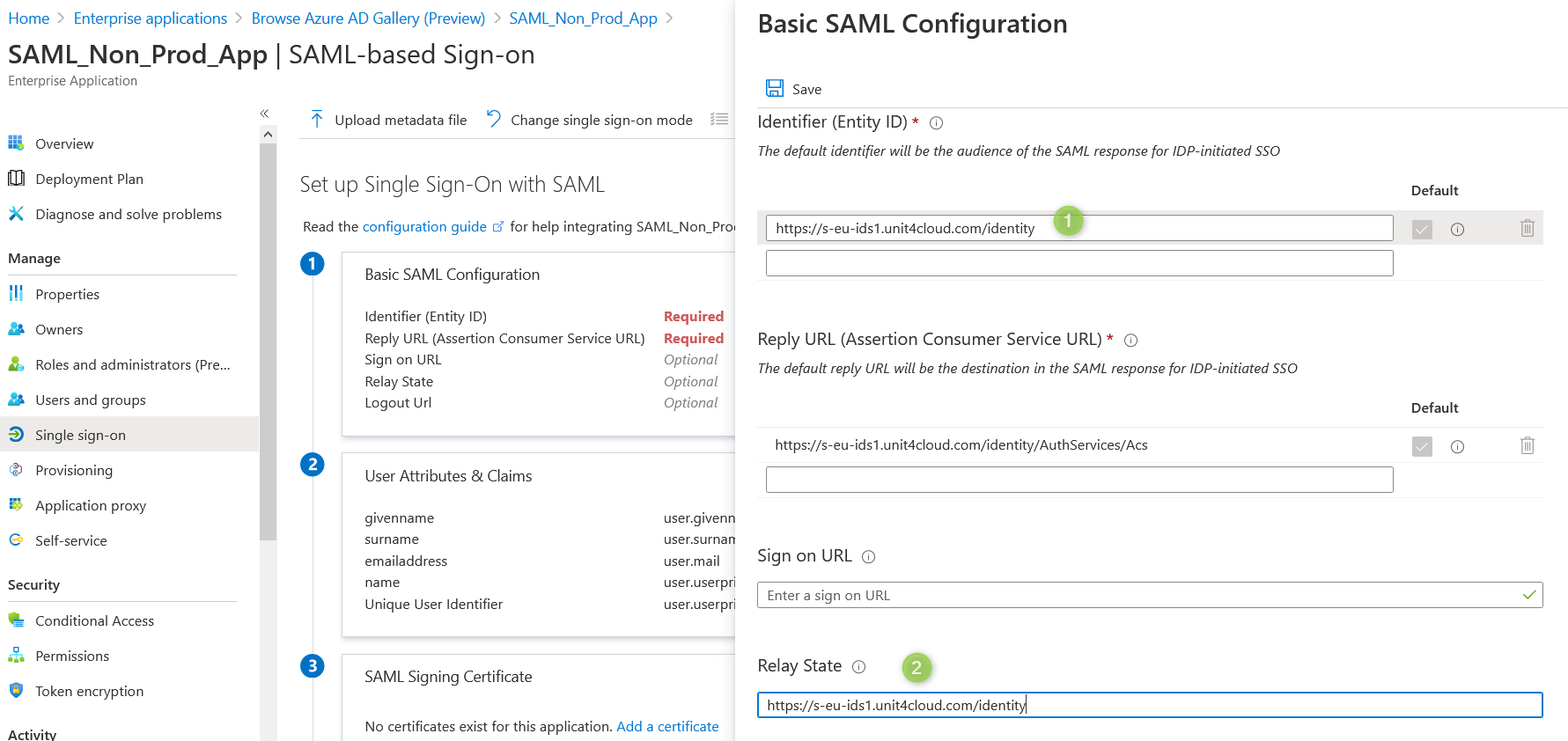
Save your changes.
Then go to the "Properties" menu and change "User assignment required?" to "NO" and save changes.
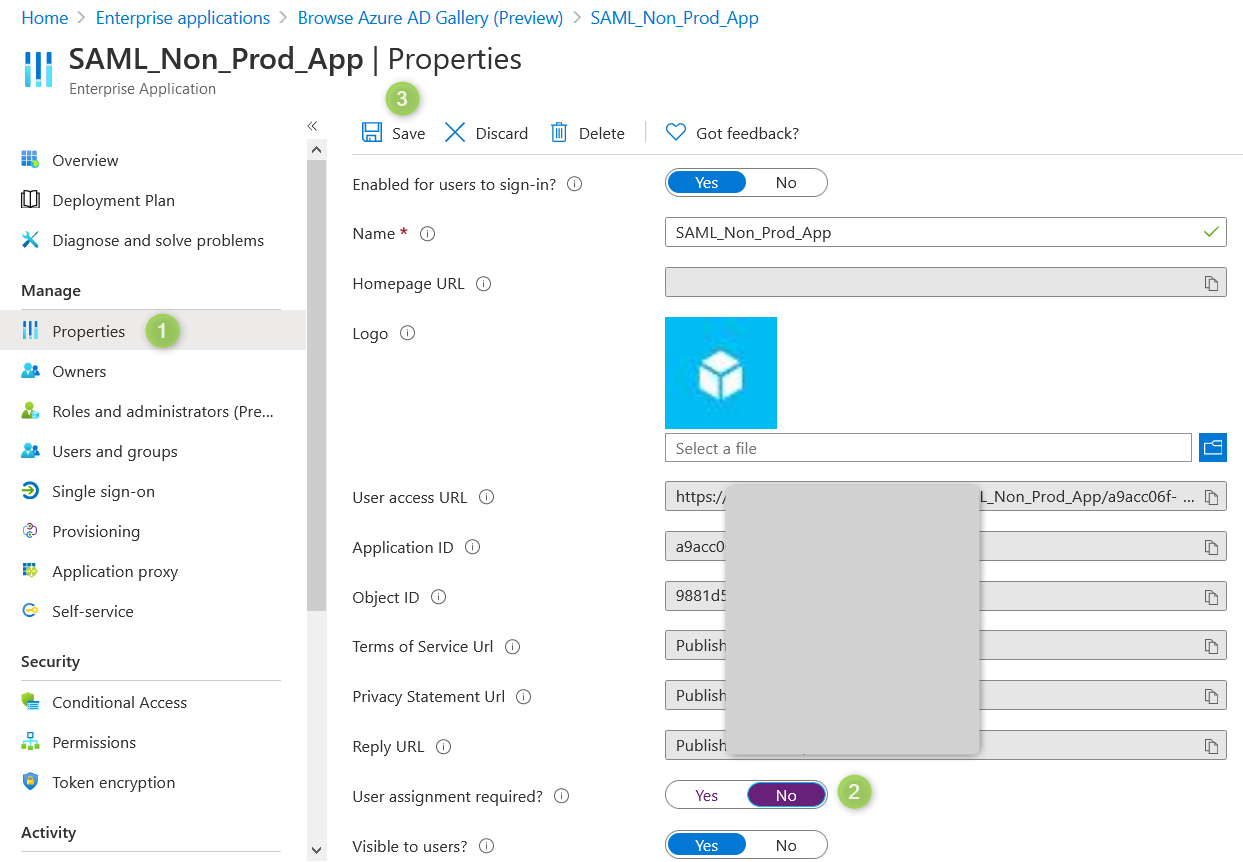
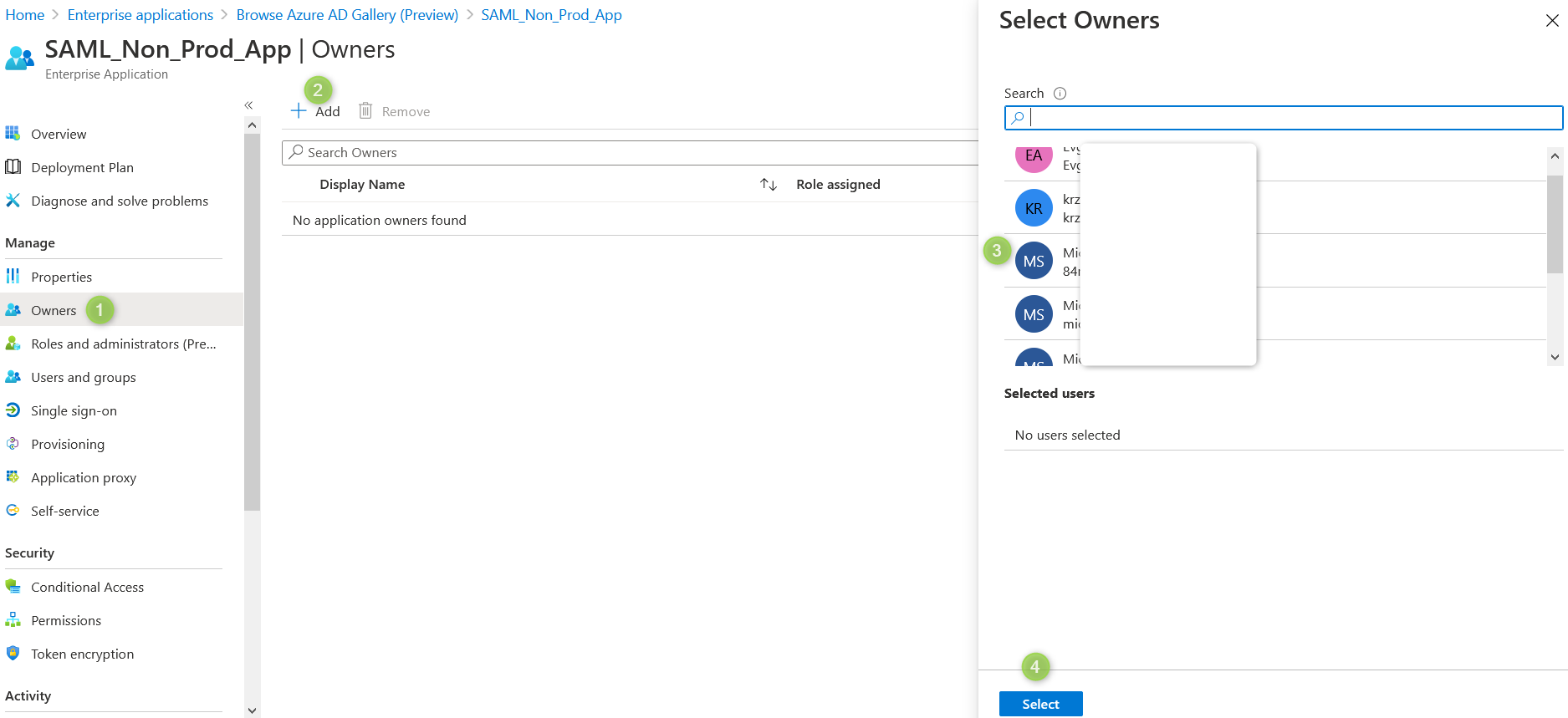
It is also recommended to assign an administrator as application owner.
Find unit4 Tenant values
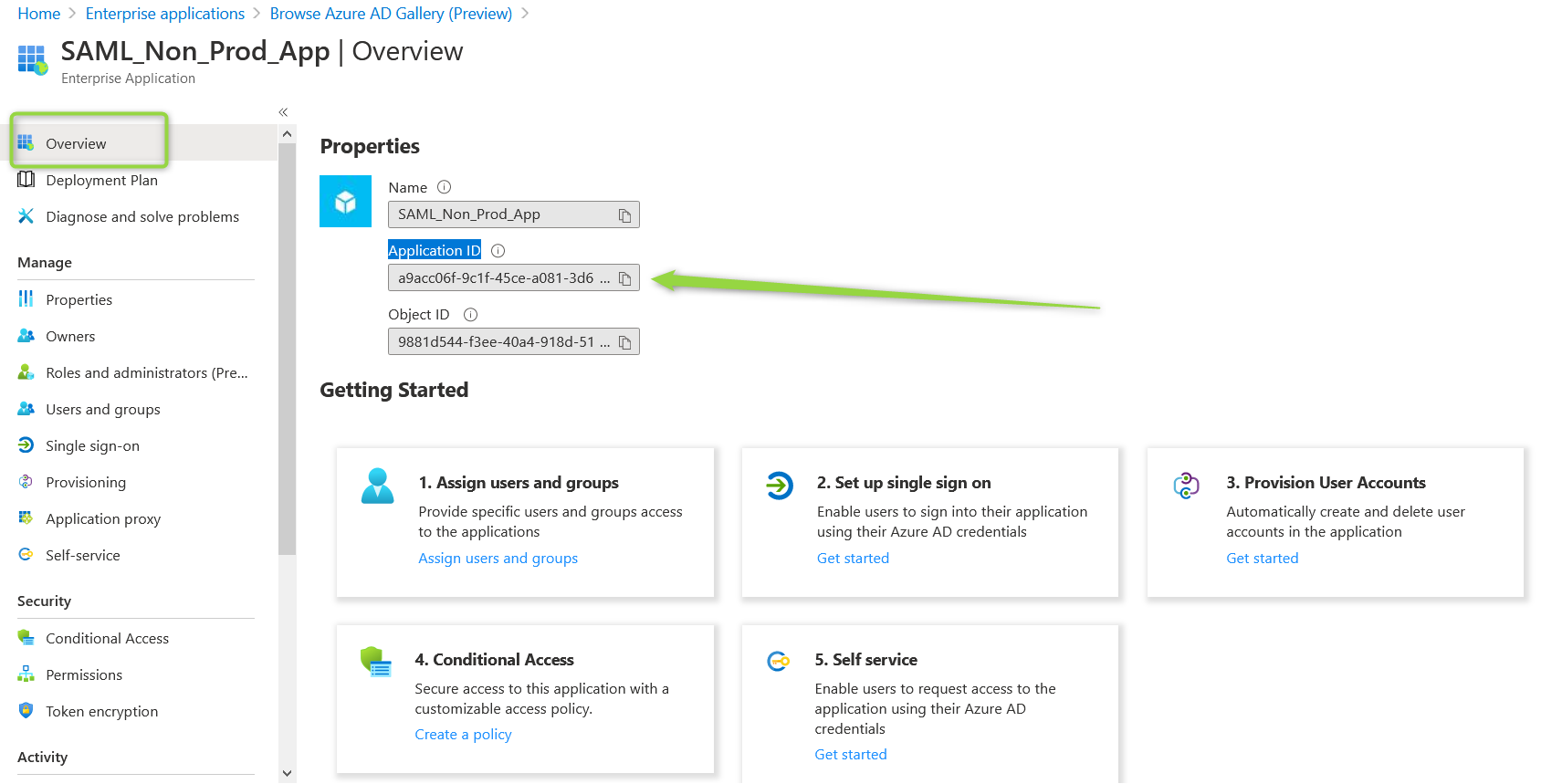
-
Application ID (you can copy it from the clipboard)
-
Authority url (ex: https://login.microsoftonline.com/5c13f575-11111111-1cab8b/federationmetadata/2007-06/federationmetadata.xml?appid=76ae6f1b-111111111-3fea) As you can see it's metadata url + Application ID
-
NameClaimType - The claim provided by the external IdP that should be mapped to the name claim returned by U4IDS. For example "Name".
-
Unit4IdClaimType - The claim provided by the external IdP that should map to the unit4_id for example "email"
Register the AAD application as a tenant in U4IDS
After the above steps are done, the collected information may be inserted into the Tenant resource in U4IDS:
{
"authority": "<your AAD Authority url>",
"idpRegId": "<your AAD Application ID>",
"nameClaimType": "name",
"protocol": "saml",
"tenantId": "<Your Unit4 tenant ID GUID>",
"unit4IdClaimType": ["email"]
}
Select a unit4IdClaimType
For the unit4IdClaimType claim type email is used in this example.
Get the authority
"Authority" is "Metadata address plus Application ID.
Get the idpRegId
The "idpRegId" in AAD is the Application ID.
